After a litte more than one month the Zimbra zmcat infection is still spreading wide! A lot of people is still reporting on Zimbra forum and on my original blog post about activities on their systems.
While the blog still remains the main source for guidelines on how to cleanup the system, nowadays infections are harder to uproot than the beginning: the attacker matured, changed file names, increased the IPs hosting the malicious scripts and so on.
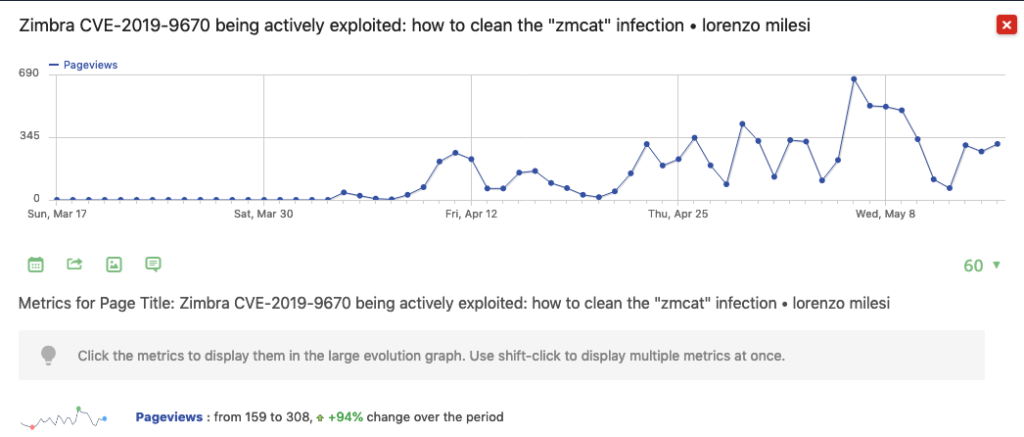
Zimbra published an advisory on March 18th, followed closely by patches for current stable, LTS and unsupported 8.6. In the first days of April zmcat started appearing on some systems.
During the early stages of infection the zmcat binary was dropped in /tmp, but was running silently. After some weeks, around mid April, it started doing what it was expected to do: mining cryptocurrency! So people found their servers running full throttle by this process, prefixed like all Zimbra commands and running as zimbra user.
Given that it was a little suspicious to have a Zimbra command in /tmp, the attacker had a cooler idea: why not placing it in /opt/zimbra? And why not giving it another name, so it will look less known? So in the end of April we witness the birth of /opt/zimbra/log/zmswatch.sh, another name for the zmcat infection. It’s the very same miner, in another name and path.
As there are still a lot of people with unpatched Zimbras which are trying to find workaround to manage the infection. My advices are:
- patch now!
- iptables blocking is futile, as well as useragent: they might let you gain some time, but you will still need to go back to 1;
- creating /tmp/zmcat as root so it cannot be written by the attacker is stupid: your server will certainly not be mining, but it will still be infected! An attacker can do whatever he wants with your Zimbra, included dumping all your mail, deleting accounts, causing whatever damage they want;
- the same applies to renaming the tools used to feed the servers, like wget: the attacker can still run zmprov and do whatever he wants with the system;
- if it’s something acceptable for you do geoblocking: by enabling only the countries your users work from you can delay the infection until you can find a timeframe for patching.
Once again: patch your Zimbra!
Try to find 2 files, zmmailboxdwatch.sh and zmsstore.sh, in /opt/zimbra/lib and in /opt/zimbra/conf, because the files copies itself in the second location.
if you edit zmsstore.conf, ypu can see the infecction comes from a github user (http://raw.githubusercontent.com/singhkarn/xmr/master/sshd), so block github in your firewall
Actually I don’t think that will work, the miner has been downloaded from other infected sites before.
And anyway you will remain vunlerable anyway.
Hi all, we are on
Release 8.7.1_GA_1670.RHEL7_64_20161025045328 RHEL7_64 NETWORK edition
I didn’t find a “patch” to this release. Do you know where I can get it?
Regards
You first have to upgrade to the latest minor release, in your case 8.7.11.
Look for these files, are virus:
/opt/zimbra/conf/zmsstore.conf
/opt/zimbra/lib/zmmailboxdwatch
/opt/zimbra/libexec/zimbra